Titan MFT Server
Managed File Transfer with automation, strong security and scalability
MFT Server Solution to Ensure Security
Titan MFT is a security-focused Managed File Transfer solution, supporting the latest encryption standards, streaming disk encryption, 2-factor authentication, and a variety of administrator tools to control access. Managed File Transfer is central to protecting files while stored or during transfer, so Titan MFT is focused on security best practices. Active Directory and LDAP are supported by Titan MFT to streamline user authentication.
Titan MFT also includes load-balancing support, multi-server clustering and fail-over, and increased file transfer speeds with top-line data compression. Events management and automation distribute work volume and facilitate workflow to save you time on vital but tedious tasks.
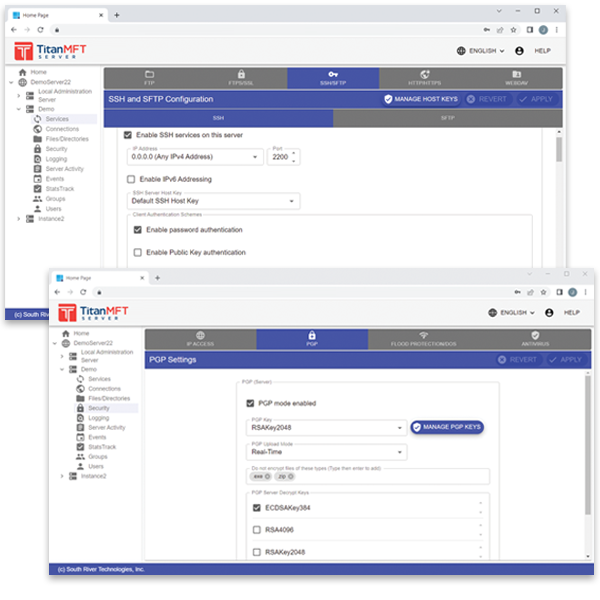
An MFT server in your control
Titan MFT builds on the Titan SFTP Server platform to bring your business a complete MFT solution. Titan MFT offers:- PGP to encrypt at-rest data without leaving data temporarily unsecured
- Support for two-factor authentication using Google and Microsoft Authenticators
- FIPS 140-2, HIPAA, PCI and Sarbanes-Oxley compliance
- Easy and secure file sharing with customers and partners
- Protection from common hacking attempts by closing inbound firewall ports, automating events
- Files can be stored on the local VM hard drive or on Azure File Storage accounts.
- Optional Titan DMZ Server protection.
- On-site, cloud, or hybrid implementation options.
- Extremely affordable pricing for all deployment options.
The New Standard for Managed File Transfer
MFT Security Controls
- Streaming Disk Encryption
- 2-Factor Authentication
- Secure Transfer Protocols
- Perimeter Security
Secure Collaboration
- Effortless file sharing with link expiration
- QuickSend Feature
- Dropzone to receive external files
Compliance
- PCI
- HIPAA
- FIPS 140-2 / GDPR
- ITAR
Supported Protocols
- FTP and HTTP with TLS
- SFTP
- WebDAV
- IPv6
Host Key Support
- Supports SSH format Keys
- Password protection of imported host keys
- Imports .pub format
Virtual Folders
- Easily Enable Access Network Directories
- Server, Group, or User Level
- Easily add a UNC path
Account Controls
- Granular Configuration
- Enable/Disable Accounts
- Settings Customization
- Account Expiration
Authentication
- Native Authentication
- Active Directory or LDAP
- Hybrid Authentication
- Trusted TLS Certificates
HA / Load Balancing
- Clustering
- Failover
- Eliminate downtime
- Simple to scale
Admin Tools
- Web-based Admin Console
- Multiple Logging Formats
- REST API and Command-line Utility
- Activity Monitor
Automation
- Over 100 Event Actions
- Scheduled or by Trigger
- AV scans, Backups, Reports
- Shut down Hackers
File Management
- Supports Compression
- Ban File Types
- Preserve or Convert Case
- Resume Transfers
Replacing your FTP solution
Managed File Transfer solutions solve the many problems associated with FTP. Titan MFT is easier to manage and more secure.- Vastly improved security of file transfers and stored files
- Advanced reporting gives you useful information on data flows and user activities
- Easy file sharing within your organization and with external partners
- High Availability for uninterrupted operations
- Automation capabilities to replace unwieldy scripts
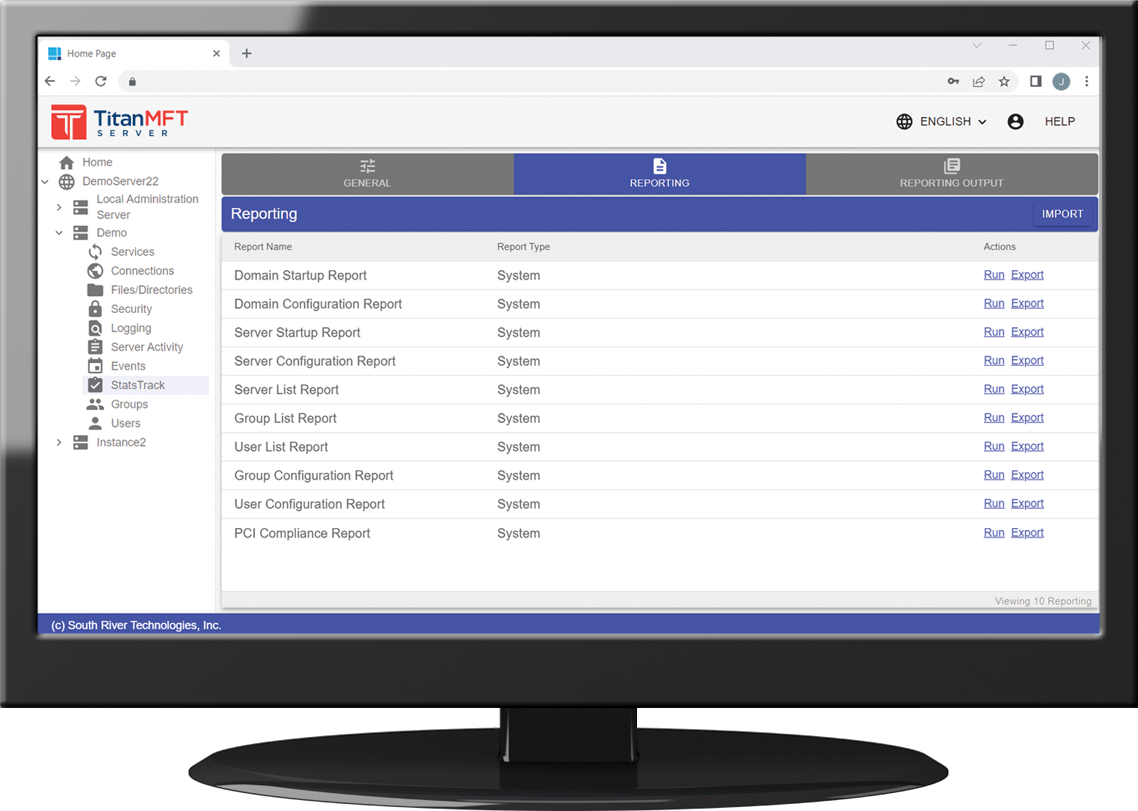

Titan MFT implementation options
We offer you a range of implementation options that can securely facilitate migration to the cloud, stand up reliable on-premises options, or customize a hybrid of both to best suit your organization’s objectives and budget. Our professional services team is available to assist you with any configuration that you choose.Cloud
A cloud implementation of Titan MFT provides security and performance, with the flexibility and lower upfront costs of a cloud solution. Easily spin up or turn off additional servers to accommodate peak processing requirements while controlling costs. Titan MFT is available in the AWS, Google and Azure marketplaces. Monthly costs are based upon your usage and specific infrastructure configuration.On-Premises
Implementing Titan MFT on-premises gives you complete control of your environment, without recurring monthly costs. Purchase a perpetual license with just annual maintenance and support as an ongoing cost. There are no additional costs for number of users, connection, storage or bandwidth.Let our Cloud Experts Help
We are here to listen to your needs and help you design, implement and optimize your cloud solutions. Whether it’s AWS, Azure, or Google Cloud, we have navigated the ins and outs and are well-versed in making the most of their features for efficient and secure operations. If you have questions or need assistance with any cloud-related file transfer need, we are here to help!
| Titan MFT Server | Monthly Cost* | Annual Cost* | Subscribe Link |
| Azure Marketplace | $65.70 ($0.09/hr) | $788.40 ($0.09/hr) | Subscribe Now |
| AWS Marketplace | $65.70 ($0.09/hr) | $788.40 ($0.09/hr) | Subscribe Now |
| Google Marketplace | $65.70 ($0.09/hr) | $788.40 ($0.09/hr) | Subscribe Now |
| Azure Marketplace | $65.70 ($0.09/hr) | $788.40 ($0.09/hr) | Subscribe Now |
| AWS Marketplace | $65.70 ($0.09/hr) | $788.40 ($0.09/hr) | Subscribe Now |
Titan MFT Server is available via the traditional, on-premise licensing model. Simply purchase the license and you can download the software to install in whatever environment best meets your requirements. View System Requirements.
Pricing below includes 1-year of email-only Maintenance and Support. 8×5 and 24×7 Phone Support options are available at an additional cost. Please contact our sales team for pricing.
Maintenance and Support renews annually.
| Operating System | Price | Purchase Link | |
| Titan MFT Server | $7,500.00 | Contact Sales | |
| Titan MFT Server | $7,500.00 | Contact Sales |
Cloud Pricing
 Windows OS
Windows OS
 Azure Marketplace
Azure Marketplace
- Monthly Cost – $65.70 ($0.09/hr)
- Annual Cost – $788.40 ($0.09/hr)
- Subscribe on Azure Now
 AWS Marketplace
AWS Marketplace
- Monthly Cost – $65.70 ($0.09/hr)
- Annual Cost – $788.40 ($0.09/hr)
- Subscribe on AWS Now
 Google Marketplace
Google Marketplace
- Monthly Cost – $65.70 ($0.09/hr)
- Annual Cost – $788.40 ($0.09/hr)
- Subscribe on Google Now
 Linux OS
Linux OS
 Azure Marketplace
Azure Marketplace
- Monthly Cost – $65.70 ($0.09/hr)
- Annual Cost – $788.40 ($0.09/hr)
- Subscribe on Azure Now
 AWS Marketplace
AWS Marketplace
- Monthly Cost – $65.70 ($0.09/hr)
- Annual Cost – $788.40 ($0.09/hr)
- Subscribe on AWS Now
On-Premises Pricing
 Windows OS
Windows OS
Titan MFT Server
- Price – $7,500.00
- Contact Sales
 Linux OS
Linux OS
Titan MFT Server
- Price – $7,500.00
- Contact Sales
Compare Titan Editions
- Titan SFTP Server
- Titan SFTP Server – HA
- Titan MFT Server
System Requirements
- Operating System
- Minimum Hardware and Software Requirements
- Product Limitations
Support Overview
- Overview of plans
- Response times
- Hours of operation

[Titan MFT] is “solid, flexible, and reliable. The software is very flexible and configurable. There are so many options we can use to make the product do pretty much anything we need it to. The ability to handle multiple protocols (SFTP, HTTP, HTTPS) make it a thorough and complete solution.”
![]()
START YOUR FREE 20-DAY TRIAL
No registration required



